Get Refresh Token
Refresh tokens are credentials used to obtain access tokens. Refresh tokens are issued to the client by the authorization server and are used to obtain a new access token when the current access token becomes invalid or expires, or to obtain additional access tokens with identical or narrower scope (access tokens may have a shorter lifetime and fewer permissions than authorized by the resource owner).
Issuing a refresh token is optional at the discretion of the authorization server. If the authorization server issues a refresh token, it is included when issuing an access token.
A refresh token is a string representing the authorization granted to the client by the resource owner. The string is usually opaque to the client. The token denotes an identifier used to retrieve the authorization information.
Unlike access tokens, refresh tokens are intended for use only with authorization servers and are never sent to resource servers.
Refresh Token Protocol Flow
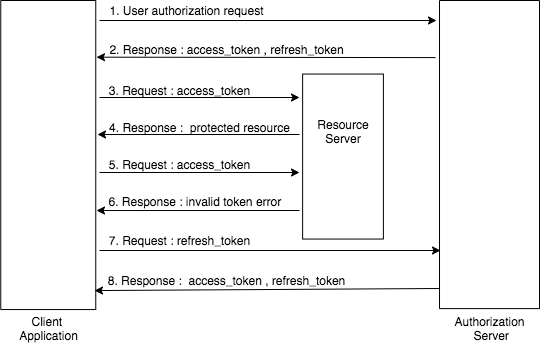
The diagram illustrates the our authentication server refresh token protocol, which is designed to allow a client application to obtain a new access token without requiring the user to reauthenticate.
This mechanism ensures continuous access while minimizing user inconvenience and improving security. Here's a detailed explanation of the protocol steps:
Key Components
- Client Application
The application interacting with the user and requesting resources. - Authorization Server
The our authorization server issuing access tokens and refresh tokens. - Resource Server
The server hosting the protected resources.
Steps In The Our Refresh Token Protocol
- User Authorization Request
The client application initiates an authorization request by directing the user to our Authorization Server.
The user logs in and consents to share their data. - Access Token and Refresh Token Response
After successful authorization, the Authorization Server issues an access token and a refresh token.
The access token is used for short-term access to protected resources.
The refresh token is a long-lived credential used to obtain new access tokens when the current one expires. - Request for Protected Resource
The client uses the access token to request a protected resource from the Resource Server.
The access token is included in the HTTP Authorization header. - Response with Protected Resource
If the access token is valid, the Resource Server responds with the requested resource. - Request with Expired Token
If the client sends a request with an expired or invalid access token, the Resource Server rejects it and returns an error. - Error Response for Invalid Token
The Resource Server indicates that the access token is no longer valid and cannot be used to access resources. - Request for a New Access Token Using the Refresh Token
The client uses the refresh token to request a new access token from the Authorization Server.
This is done via a POST request to the token endpoint. - New Access Token and Refresh Token Response
The Authorization Server validates the refresh token. If valid, it issues a new access token and, optionally, a new refresh token.
The client can now use the new access token to request resources.
Key Benefits of the Refresh Token Protocol
- Improved Security
- Access tokens are short-lived, reducing the risk of misuse.
- Long-lived refresh tokens can be securely stored on the client-side.
- Better User Experience
Users do not need to log in repeatedly when access tokens expire. - Scalability
Reduces load on our Authorization Server, as users authenticate less frequently.
Error Handling in Refresh Token Flow
- Invalid Refresh Token
If the refresh token is expired, revoked, or invalid, the server returns an error, and the user must reauthenticate. - Access Denied
If the client provides incorrect credentials, the Authorization Server denies the request.
Updated 9 months ago