Get Access Token
Obtain Your Access Token for Secure API Authentication
An access token is a credential issued by the authorization server that allows clients to authenticate and access protected resources. To retrieve an access token, your client must send a request to our authorization server. This token will be used to authorize all your API calls to our resource servers, ensuring secure access to the desired data.
An access token is a string representing an authorization issued to the client. The string is usually opaque to the client. Tokens represent specific scopes and durations of access, granted by the resource owner, and enforced by the resource server and authorization
server.
The token may denote an identifier used to retrieve the authorization information or may self-contain the authorization information in a verifiable manner (i.e., a token string consisting of some data and a signature).
The access token provides an abstraction layer, replacing different authorization constructs (e.g., username and password) with a single token understood by the resource server. This abstraction enables issuing access tokens more restrictive than the authorization grant used to obtain them, as well as removing the resource server's need to understand a wide range of authentication methods.
Access tokens can have different formats, structures, and methods of utilization (e.g., cryptographic properties) based on the resource server security requirements.
Access Token Protocol Flow
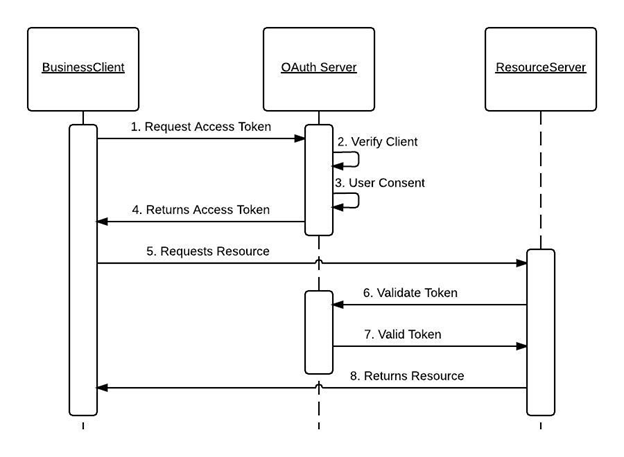
The image shows the OAuth 2.0 access token protocol flow, which outlines the process for a client application to obtain an access token and use it to access protected resources on behalf of a user. Here's a detailed explanation of each step in the flow:
Key Components
- Business Client
The application or client requesting access to protected resources (e.g., a web or mobile app). - OAuth Server
The SIL (Savannah Informatics Limited) authorization server responsible for issuing access tokens after authenticating the client and user. - Resource Server
The server hosting the protected resources (e.g., user data).
Steps in the OAuth 2.0 Access Token Protocol
- Request Access Token
The client (Business Client) sends a request to the OAuth Server to obtain an access token.
This request usually includes the client credentials (e.g., client ID and client secret) and, depending on our grant type, user credentials. - Verify Client
The OAuth Server validates the client’s identity using the provided client ID and secret.
If applicable, it also verifies the validity of the user credentials. - User Consent
The OAuth Server may ask the user to approve the requested permissions. This step ensures the user agrees to share their data with the client. Once consent is given, the OAuth Server proceeds with token generation. - Returns Access Token
If the client and user credentials are valid, the OAuth Server generates an access token and sends it back to the client.
The response includes the access token, token type, expiration time, and optionally a refresh token. - Request Resource
The client uses the access token to request a protected resource from the Resource Server.
The access token is included in the Authorization header of the HTTP request. - Validate Token
The Resource Server validates the access token with the OAuth Server to ensure it is valid, has not expired, and matches the requested resource's scope. - Valid Token
If the access token is valid, the OAuth Server confirms its authenticity to the Resource Server. - Returns Resource
The Resource Server provides the requested resource to the client.
If the token is invalid or expired, an error response is returned instead.
Updated 7 months ago